Advertisement
Rampant Ransomware Attacks: How Cybercriminals Target Governments
Resume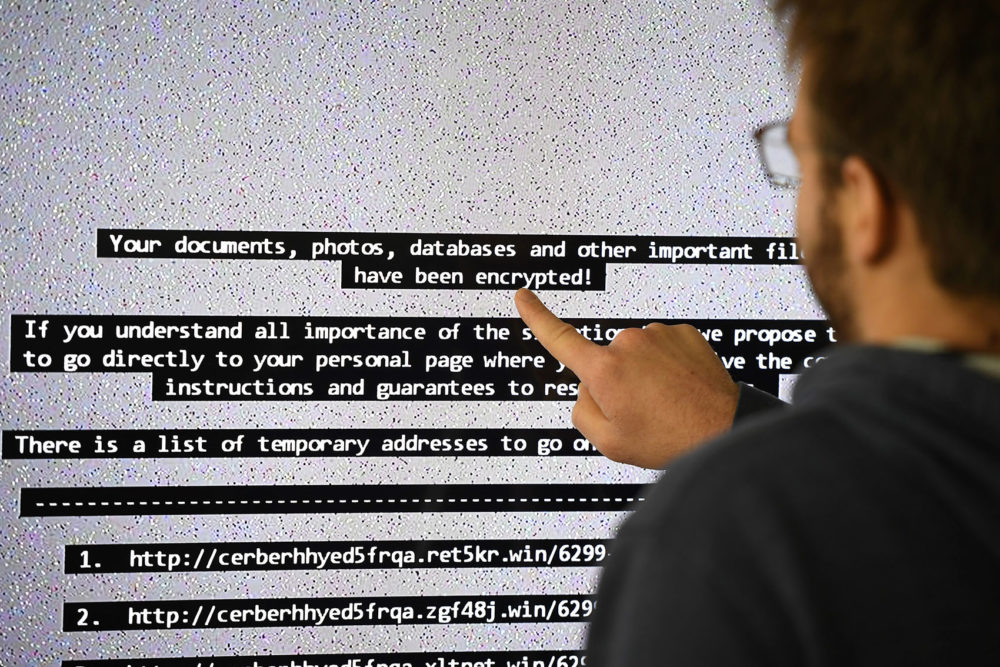
With Jane Clayson
Across the country, cybercriminals are locking up local government files until ransom is paid. We look at the growing threat of ransomware attacks.
Guests
Frances Robles, national and foreign correspondent for The New York Times based in Miami. (@FrancesRobles)
Tyler Moore, professor of cybersecurity and information assurance at the Tandy School of Computer Science at the University of Tulsa. Director of StopBadware, a nonprofit anti-malware organization. (@TylerWMoore)
From The Reading List
FBI Statement On Ransomware Attacks
The FBI encourages victims to not pay a hacker’s extortion demands. The payment of extortion demands encourages continued criminal activity, leads to other victimizations, and can be used to facilitate additional serious crimes. Additionally, paying a ransom does not guarantee the victim will regain access to their data. The best approach is to focus on defense in depth and have several layers of security as there is no single method to prevent compromise or exploitation. The main thrust of the FBI’s ransomware outreach program is to inform the public that most ransomware can be prevented by taking steps such as updating your Operating System to the latest version and shortening your patch cycles, using multifactor authentication and complex unique passwords for each login, and disabling any unnecessary network services. Similarly, the cost imposed by ransomware can be abated by maintaining offline backups of any critical data.
New York Times: "A City Paid a Hefty Ransom to Hackers. But Its Pains Are Far From Over." — "Audrey Sikes, city clerk of Lake City, Fla., has a thing for documents: She does not like losing them.
"It falls to Ms. Sikes, as official custodian of records for this city of 12,000 people about an hour west of Jacksonville, to maintain Lake City’s archives. She keeps a log of public record requests and has spreadsheets that track things like property deeds and building permits. She spent years digitizing all the papers of a city that incorporated before the Civil War.
"'It’s everything I do,' Ms. Sikes said.
"Did.
"More than 100 years’ worth of municipal records, from ordinances to meeting minutes to resolutions and City Council agendas, have been locked in cyberspace for nearly a month, hijacked by unidentified hackers who encrypted the city’s computer systems and demanded more than $460,000 in ransom.
"Weeks after the city’s insurer paid the ransom, the phones are back on and email is once again working, but the city has still not recovered all of its files. There is a possibility that thousands of pages of documents that had been painstakingly digitized by Ms. Sikes and her team will have to be manually scanned, again."
Washington Post: "The Baltimore ransomware attack could be coming to your city — or hospital" -- "It is tempting to view cybercriminals as extremely clever, capable of breaking through the strongest defenses put in front of them. The reality is that they often aren’t, if for no other reason than they don’t need to be.
"The May 7 ransomware attack that has paralyzed Baltimore’s city government for much of this month is a case in point. It is true, as the New York Times reported May 25, that the attack used a hacking tool developed by the National Security Agency that is now being exploited by criminals and state actors. Nonetheless, basic cyber-hygiene, were it in place, could have greatly limited the damage in Baltimore or stopped the attack altogether. The ransomware, called RobinHood, worked only because city computers had not applied freely available software patches and were operating without effective backups.
"Despite the preventable nature of the attack, the costs to Baltimore are very real and continue to mount. Essential city services, from obtaining permits to closing home sales, have been unavailable. The problem has frustrated Baltimore residents and inhibited commerce."
CNN: "Crippling ransomware attacks targeting US cities on the rise" -- "Targeted ransomware attacks on local US government entities — cities, police stations and schools — are on the rise, costing localities millions as some pay off the perpetrators in an effort to untangle themselves and restore vital systems.
"The tally by cybersecurity firm Recorded Future — one of the first efforts to measure the breadth of the assaults — found that at least 170 county, city or state government systems have been attacked since 2013, including at least 45 police and sheriff's offices.
"The firm compiled all known instances of ransomware infections of local government systems, a type of cyberattack that encrypts a computer's files, where the attacker demands payment --usually in bitcoin — for a key to unlock them.
"The federal government and the FBI do not track the attacks nationwide."
Wired: "Ransomware hits Georgia courts as municipal attacks spread" --- "Ransomware has no shortage of cautionary tales and wakeup calls from the past decade. But for local governments, this past year has been a particularly brutal reminder of the threat. Following a 2018 attack that paralyzed the City of Atlanta for weeks, more than half a dozen cities and public services across the country have fallen to ransomware so far in 2019, on a near-monthly basis; the Administrative Office of the Georgia Courts became the latest victim on Saturday, when an attack knocked its systems offline.
"The string of attacks on municipalities may seem like a new pattern. But it’s unclear how many of them, if any, were perpetrated by the same actors. And law enforcement officials emphasize that the spate of attacks actually fits into a broader, ever-growing trend of ransomware attacks that spans numerous industry sectors.
" 'We are seeing an increase in targeted ransomware attacks; however, we do not have enough data to indicate one industry or sector is being targeted more than another,' the FBI told WIRED in a statement. 'Cyber criminals are opportunistic. They will monetize any network to the fullest extent.'
"Incident responders agree with this assessment and note that attackers will capitalize on any technique that sees some success, to infect as many targets as possible and maximize the possibility of return."
Anna Bauman produced these segments for broadcast.
This segment aired on July 9, 2019.